Firewall On Red Hat Linux
To list all services available on the system:
[root@linux ~]# firewall-cmd --get-services
RH-Satellite-6 amanda-client bacula bacula-client cups dhcp dhcpv6 dhcpv6-client dns freeipa-ldap freeipa-ldaps freeipa-replication ftp high-availability http https imaps ipp ipp-client ipsec iscsi-target kerberos kpasswd ldap ldaps libvirt libvirt-tls mdns mountd ms-wbt mysql nfs ntp openvpn pmcd pmproxy pmwebapi pmwebapis pop3s postgresql proxy-dhcp radius rpc-bind rsyncd samba samba-client smtp ssh telnet tftp tftp-client transmission-client vdsm vnc-server wbem-https
To list all zones available on the system:
[root@linux ~]# firewall-cmd --get-zones
block dmz drop external Home internal public trusted work.
To list the default zone of your system:
[root@linux ~]# firewall-cmd --get-default-zone
public
To list all the zones:
[root@linux ~]# firewall-cmd --list-all-zones
block
interfaces:
sources:
services:
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
dmz
interfaces:
sources:
services: ssh
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
drop
interfaces:
sources:
services:
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
external
interfaces:
sources:
services: ssh
ports:
masquerade: yes
forward-ports:
icmp-blocks:
rich rules:
home
interfaces:
sources:
services: dhcpv6-client ipp-client mdns samba-client ssh
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
internal
interfaces:
sources:
services: dhcpv6-client ipp-client mdns samba-client ssh
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
public (default, active)
interfaces: eno16777984
sources:
services:
ports:
masquerade: no
forward-ports:
icmp-blocks: echo-reply echo-request
rich rules:
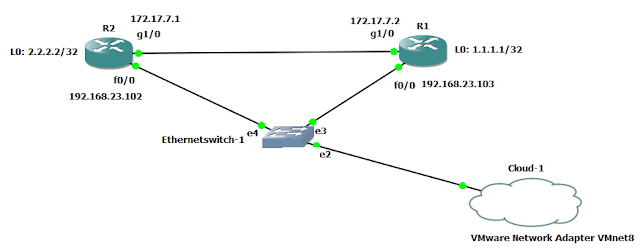
rule family="ipv4" source address="172.17.7.0/24" port port="513" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="23" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="20048" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="631" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="21" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="513" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="53048" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="20" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="23" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="631" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="111" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="22" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="53048" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="53" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="20048" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="20" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="53" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="21" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="111" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="22" protocol="tcp" accept
trusted
interfaces:
sources: 172.0.0.0/8
services:
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
work
interfaces:
sources:
services: dhcpv6-client ipp-client ssh
ports:
masquerade: no
forward-ports:
icmp-blocks:
rich rules:
To set a Default Zone:
[root@linux ~]# firewall-cmd --set-default-zone=internal
Success
Verify the default zone.
[root@linux ~]# firewall-cmd --get-default-zone
internal
To open port 8080 on TCP not persistent on DMZ zone:
[root@linux ~]# firewall-cmd --zone=dmz --add-port=8080/tcp
To open port 8080 on TCP with persistent on DMZ zone:[root@linux ~]# firewall-cmd --zone=dmz --add-port=8080/tcp --permanent
To open ports with udp in the same step on zone public: [root@linux ~]# firewall-cmd --zone=public -add-port=5060-5061/udp
List all ports opening on zone public:[root@linux ~]# firewall-cmd --zone=public --list-all
public (default, active)
interfaces: eno16777984
sources:
services:
ports:
masquerade: no
forward-ports:
icmp-blocks: echo-reply echo-request
rich rules:
rule family="ipv4" source address="172.17.7.0/24" port port="513" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="23" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="20048" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="631" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="21" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="513" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="53048" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="20" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="23" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="631" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="111" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="22" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="53048" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="53" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="20048" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="20" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="53" protocol="tcp" accept
rule family="ipv4" source address="172.17.7.0/24" port port="21" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="111" protocol="tcp" accept
rule family="ipv4" source address="172.17.82.0/24" port port="22" protocol="tcp" accept
To open port 80 for public zone permanent:
[root@linux ~]# firewall-cmd --permanent --zone=public --add-port=80/tcp
To remove added port, just use the ‘–remove‘ option with firewalld command:
[root@linux ~]# firewall-cmd --zone=public --remove-port=80/tcp
To block Incoming and Outgoing Packets (Panic Mode):If you wish to block any incoming or outgoing connections, you need to use a ‘panic-on‘ mode to block such requests. For example, the following rule will drop any existing established connection on the system.
[root@linux ~]# firewall-cmd --panic-on
[root@linux ~]# ping google.com -c 1
Failure
[root@linux ~]# firewall-cmd --query-panic
yes
To allow Incoming and Outgoing Packets (Panic Mode)
[root@linux ~]# firewall-cmd --panic-off
[root@linux ~]# ping google.com -c 1
Success
To block without any messages use DROP as Jump to target.
[root@linux ~]# firewall-cmd -A INPUT -p icmp --icmp-type echo-request -j DROP
[root@linux ~]# firewall-cmd -A OUTPUT -p icmp --icmp-type echo-replay -j DROP
To using iptables zones by firewalld:
allow incoming port 80 on tcp and deny other.
[root@linux ~]# firewall-cmd --permanent --direct --add-rule ipv4 filter OUTPUT 0 -p tcp -m tcp --dport=80 -j ACCEPT
[rrot@linux ~]# firewall-cmd --permanent --direct --add-rule ipv4 filter OUTPUT 1 -j DROP
------------------------------------------------------------------------------------------------------------
Good Luck
https://www.linkedin.com/in/ahmedms/

Comments
Post a Comment